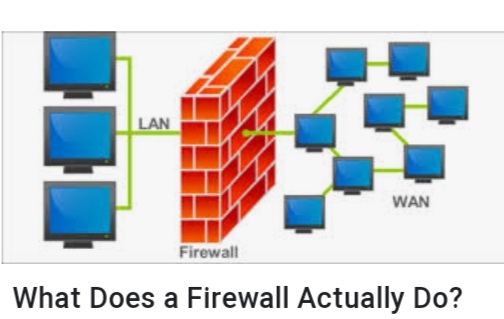
A firewall sits between a computer (or local network) and another network (such as the Internet), controlling the incoming and outgoing network traffic. Without a firewall, anything goes. With a firewall, the firewall’s rules determine which traffic is allowed through and which isn’t.
What is a firewall? Firewalls explained and why you need one
- A firewall sits between a computer (or local network) and another network (such as the Internet), controlling the incoming and outgoing network traffic. Without a firewall, anything goes. With a firewall, the firewall’s rules determine which traffic is allowed through and which isn’t.
- A firewall is recognized as the first line of defense in securing sensitive information. For better safety, the data can be encrypted.
- A firewall can help protect your computer and data by managing your network traffic. It does this by blocking unsolicited and unwanted incoming network traffic. A firewall validates access by assessing this incoming traffic for anything malicious like hackers and malware that could infect your computer.
- A firewall is a security device — computer hardware or software — that can help protect your network by filtering traffic and blocking outsiders from gaining unauthorized access to the private data on your computer.
- Not only does a firewall block unwanted traffic, it can also help block malicious software from infecting your computer.
- Firewalls can provide different levels of protection. The key is determining how much protection you need.
- The topics below can help you learn what firewalls do and determine the level of protection that will help keep your computer and the data on it safe and secure.
What does a firewall do?
A firewall acts as a gatekeeper. It monitors attempts to gain access to your operating system and blocks unwanted traffic or unrecognized sources.
How does it do this? A firewall acts as a barrier or filter between your computer and another network such as the internet. You could think of a firewall as a traffic controller. It helps to protect your network and information by managing your network traffic. This includes blocking unsolicited incoming network traffic and validating access by assessing network traffic for anything malicious like hackers and malware.
Your operating system and your security software usually come with a pre-installed firewall. It’s a good idea to make sure those features are turned on. Also, check your security settings to be sure they are configured to run updates automatically.
How does a firewall work?
To start, a firewalled system analyzes network traffic based on rules. A firewall only welcomes those incoming connections that it has been configured to accept. It does this by allowing or blocking specific data packets — units of communication you send over digital networks — based on pre-established security rules.
A firewall works like a traffic guard at your computer’s entry point, or port. Only trusted sources, or IP addresses, are allowed in. IP addresses are important because they identify a computer or source, just like your postal address identifies where you live.
Types of firewalls
There are software and hardware firewalls. Each format serves a different but important purpose. A hardware firewall is physical, like a broadband router — stored between your network and gateway. A software firewall is internal — a program on your computer that works through port numbers and applications.
There also are cloud-based firewalls, known as Firewall as a Service (FaaS). One benefit of cloud-based firewalls is that they can grow with your organization and, similar to hardware firewalls, do well with perimeter security.
There are several different types of firewalls based on their structure and functionality. Here are the various firewalls you can implement, depending on the size of your network and the level of security you need.
Packet-filtering firewalls
A packet-filtering firewall is a management program that can block network traffic IP protocol, an IP address, and a port number. This type of firewall is the most basic form of protection and is meant for smaller networks.
But beware. While packet-filtering firewalls can be helpful, they also have limitations. Because all web traffic is allowed, a packet-filtering firewall doesn’t block web-based attacks. So, you need additional protection to distinguish between friendly and malicious web traffic.
Proxy service firewalls
The proxy service firewall is a system that can help protect your network security by filtering messages at the application layer. It essentially serves as a gateway or middle man between your internal network and outside servers on the web. Also known as a gateway firewall, it is more secure in its use of stateful and deep packet inspection technology to analyze incoming traffic.
Stateful multi-layer inspection (SMLI) firewalls
The stateful multi-layer inspection firewall has standard firewall capabilities and keeps track of established connections. It filters traffic based on state, port, and protocol, along with administrator-defined rules and context. This involves using data from prior connections and packets from the same connection.
Most firewalls rely on stateful packet inspection to keep track of all internal traffic. This firewall is a step above packet-filtering in its use of multi-layer monitoring.
However, it is still unable to distinguish between good and bad web traffic, so you may need additional software.
Unified threat management (UTM) firewalls
A unified threat management firewall is a program that combines the functions of the SMLI firewall with intrusion prevention and antivirus. Additional services like cloud management may be included under the UTM umbrella of services.
Next-generation firewalls (NGFW)
Next-generation firewalls are more sophisticated than packet-filteringand stateful inspection firewalls. Why? They have more levels of security, going beyond standard packet-filtering to inspect a packet in its entirety. That means inspecting not just the packet header, but also a packet’s contents and source. NGFW are able to block more sophisticated and evolving security threats like advanced malware.
Network address translation (NAT) firewalls
A NAT firewall is able to assess internet traffic and block unsolicited communications. In other words, it only accepts inbound web traffic if a device on your private network solicited it.
Virtual firewalls
A virtual firewall is an appliance used in a cloud-based system, both private and public. This type of firewall is used to assess and manage internet traffic over both physical and virtual networks.
Host-based firewalls versus network-based firewalls
There are differences between host-based and network-based firewalls, along with benefits of having both in place.
Network firewalls filter traffic going to and from the internet to secured local area networks (LAN). They typically are used by businesses that need to protect a large network of computers, servers, and employees. A network-based firewall is able to monitor communications between a company’s computers and outside sources, as well as restrict certain websites, IP addresses, or other services.
Host-based firewalls work similarly but are stored locally on a single computer or device. A host-based firewall is a software application or a suite of applications that allows for more customization. They are installed on each server, control incoming and outgoing traffic, decide whether to allow traffic to individual devices, and protect the host.
Firewall history
Firewalls have certainly evolved over the years and become more advanced since the technology first entered the scene. Getting their start as a basic packet-filtering system in the late 1980’s, firewalls monitored packets sent between computers. They now offer more advanced protection and technology, as highlighted in this timeline.
- In late 1980, first generation firewalls developed as attacks on personal computers drove anti-virus products.
- In mid-1990, internet attacks on networks led to the advent of the second generation firewall; the first stateful inspection firewall was introduced in 1993.
- In early 2000, third generation firewalls addressed vulnerability exploits at the application layer, leading to Intrusion Prevention Systems Products (IPS).
- In 2010, increases in targeted attacks instigated anti-bot and sandboxing products.
- In 2017, larger scale attacks drove even more advanced protection.
Do you need a firewall at home?
Firewalls represent a first line of defense in home network security. Your home network is only as secure as its least protected device. That’s where a network security system comes in.
A firewall shouldn’t be your only consideration for securing your home network. It’s important to make sure all of your internet-enabled devices — including mobile devices — have the latest operating system, web browsers, and security software.
Another consideration? Securing your wireless router. This might include changing the name of your router from the default ID and password it came with from the manufacturer, reviewing your security options, and setting up a guest network for visitors to your home.
Why do we need firewalls?
You might already engage in certain safe computer and internet use practices, including these:
- You don’t click on unknown links or attachments.
- You only log on to trustworthy, known websites.
- You never give out any personal information unless it is absolutely necessary.
- You have strong, unique, complex passwords for each online account that you update often.
Does all of this make you safe enough? The answer may be “no.” If you use the internet, it’s smart to have a firewall in place. Cyberthreats are widespread and evolving. It’s important to use available defenses to help protect your network, and the personal information stored on your computer, against cybercrimes.
Here are the three main risks of not having a firewall:
Open access
Without a firewall, you’re accepting every connection into your network from anyone. You wouldn’t have any way to detect incoming threats. That could leave your devices vulnerable to malicious users.
Lost or compromised data
Not having a firewall could leave your devices exposed, which could allow someone to gain control over your computer or network. Cybercriminals could delete your data. Or they could use it to commit identity theft or financial fraud.
Network crashes
Without a firewall, attackers could shut down your network. Getting it running again, and attempting to recover your stored data, could involve your time and money.
Firewalls are a key part of security technology, especially when the different types of firewalls work together to provide an umbrella of protection. Firewalls can help keep your network, computer, and data safe and secure.
Frequently Asked Questions About Firewalls
What is a firewall?
A firewall is a security device in the form of computer hardware or software. It can help protect your network by acting as an intermediary between your internal network and outside traffic. It monitors attempts to gain access to your operating system and blocks unwanted incoming traffic and unrecognized sources.
How do firewalls work?
A firewall acts as a barrier or gatekeeper between your computer and another network like the internet. It works like a traffic controller, monitoring and filtering traffic that wants to gain access to your operating system.
What does a firewall protect against?
A firewall can help protect your computer and data by managing your network traffic. It does this by blocking unsolicited and unwanted incoming network traffic. A firewall validates access by assessing this incoming traffic for anything malicious like hackers and malware that could infect your computer.
What are the types of firewalls?
As listed in detail above, there are software and hardware firewalls – several different types based on their structure and functionality. A hardware firewall is physical, stored between your network and gateway. A software firewall is an internal program on your computer that works through port numbers and applications.
Do you need a firewall?
If you use the internet, it’s smart to have a firewall in place. They provide a first line of defense to help protect your computer and your personal information from cyberthreats, which are widespread and evolving.
Can a firewall be hacked?
A firewall shouldn’t be your only consideration for securing your home network. It’s important to make sure all of your internet-enabled devices have the latest operating system, web browsers, and security software. You also should secure your wireless router. This might include changing the name of your router from the default ID and password it came with from the manufacturer, reviewing your security options, and setting up a guest network for visitors to your home.
Do firewalls prevent viruses?
Firewalls manage access to your network, whereas antivirus software serves as cyber protection from malicious viruses.
What is the difference between hardware firewalls and software firewalls?
A hardware firewall is physical, like a broadband router — stored between your network and gateway. A software firewall is internal — a program on your computer that works through port numbers and applications.
Do you need a firewall at home?
Yes. Without a firewall, you could leave yourself open to accepting every connection into your home network. You wouldn’t have any way to detect incoming threats. This open access could leave your devices and personal information exposed and vulnerable to being accessed and used for malicious purposes. Those intruders could engage in malicious activities like gaining control over your computer or network, deleting your data, or using your personal information to commit identity theft and other online frauds.
Cloud Access Security Broker: Would You Like To Know More About CASB?
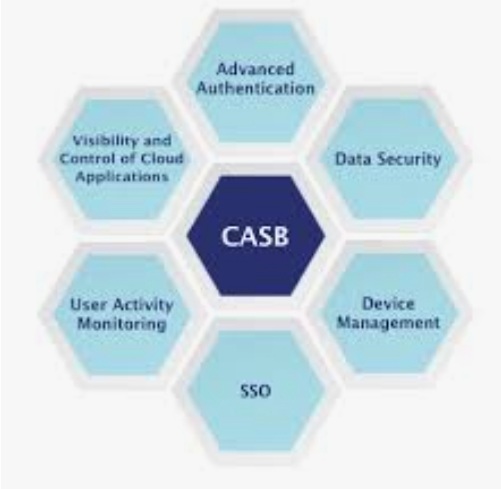
- A Cloud Access Security Broker (CASB) is the technology that mediates data between in-house IT architecture and cloud vendor environments
What does A Cloud Access Security Broker (CASB) mean?
A Cloud Access Security Broker (CASB) is the technology that mediates data between in-house IT architecture and cloud vendor environments
Although the term cloud access security broker may be used by some IT professionals to refer to companies that offer cloud brokering services, it is most often used to refer to a range of technologies that help encrypt or otherwise handle data to make it more secure in a cloud environment.
Pronounced “kazz-be”
Cloud Access Security Broker (CASB)
A cloud access security broker sits between an internal system and an external system to provide services for securing outbound data.
Cloud access security broker technologies often have a various features built into the design. These include auditing tools, tools for data loss prevention, encryption tools and monitoring tools. In a general sense, CASBs help shield enterprise systems against various types of cyber-threats by providing services such such as malware prevention as well as data security that makes data streams unreadable by outside parties. An example of a CASB technology is the cloud encryption gatewat; here the gateway service takes data at the point of egress and encrypts it for security purposes.
4 Points of High Level Conversations:
- Monitor
- Identify
- Isolate
- Eradicate
A Note from the Editor: Technology sales has been an impressive industry for me as I help solve unique challenges for customers. Working for a technology company to sell their products and services to help improve the efficiency of other businesses. If you’re looking for a technology sales rep, I’m your guy! I understand the importance the major responsibilities of the job and the advantages of the career. If you read more of this site, I will discuss what technology sales is, what a technology salesperson does.




