Computer security, cybersecurity, or information technology security protection of computer systems and networks from information disclosure, theft of or damage to their hardware, software, or electronic data, as well as from disruption or misdirection of the services they provide are big topics of discussion today.
As a Technology Sales Representative, I have achieved successfully Information Technology case projects for customers. Asking the right questions and offering solutions to:
- CISO
- VP/Director of InfoSec
- Chief Security Officer
- Senior Security Analysts
- CIO
- IT Director
- Senior Systems Administrators
- Senior Security Engineer
- Security Architect
I am always focused on making a connection (not selling), and see if they are willing to offer up on opinion. I always ” ask the security leader to give their take on the product or marketing message”. ” Make it clear that I am NOT there to sell to them, but to solicit their feedback on whether this technology is useful and interesting”.
Some of the best vendor relationships I have developed because I have a colleague who uses their product and highly recommends it. It’s one thing for a sales person to give a good demo, it’s another to hear from someone I trust that their product works on a day-to-day basis.”
ASK Non- Threatening Questions
Everything You Need to Know About Cybersecurity Attacks and How to Prevent Them
- What is Cybersecurity
- Types of Cyber Attacks
- Phishing Attack
- Man in the Middle Attacks
- SQL Injection Threat
- Distributed Denial of Service
- Drive by Attack
- Cross Site Scripting
- Password Attack
- Ransomware Attack
- Eavesdropping Attack
- AI-powered Attack
- Malware
- Zero-day exploit
- Advanced Persistent Threats
- Sources of cyber threats
- Impact of Cybersecurity
- Importance of Cybersecurity
What is cybersecurity?
Cybersecurity is a very broad category which encompasses numerous hardware and software technologies, and can be applied on any level, including personnel, corporate or governmental devices and networks.
Passwords are a cybersecurity tool that people encounter nearly every day. Other common cybersecurity tools include:
- Anti-virus/anti-malware software
- Software patches
- Firewalls
- Two-factor authentication
- Encryption
A cybersecurity plan is critical for any company with highly sensitive information. Many companies now appoint a chief security officer (CISO) to oversee their cybersecuCybersecurity is defined as the practice of protecting systems, networks, and programs from digital or virtual attacks. These cyber-attacks tend to access, change or even destroy sensitive information to the extent of extorting money from users or causally interrupt a normal business process. It is necessary to implement effective cybersecurity measures, considering the innovations in these attacks, and the upward graph of technology and its tools today.
Not so long ago, cybersecurity attacks were solely the problem of techies. However, things have changed since, and no one can afford to ignore the importance of cybersecurity. Gadgets, phones, and anything that can be connected to a computer or the internet are susceptible to cyber-attacks from criminals. The possibility of data breaches, losing confidential information, and tarnishing the image of a business heightens with these attacks. Therefore, it is crucial that you know the types of cyber threats and how to buff up your cybersecurity to prevent them.
Types of Cyber-attacks
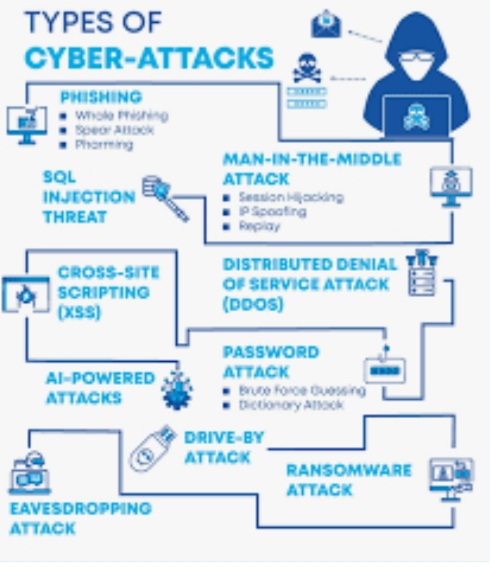
A cyber-attack is an intentional activity that exploits computers, networks, and enterprises that rely heavily on technology. Cybercriminals use malicious codes to alter the data, logic, or code on the computer.
Top 13 types of Cyber-Security Attacks
Jargon for IT Professionals
- Phishing Attack
- Man in the Middle Attacks
- SQL Injection Threat
- Distributed Denial of Service
- Drive by Attack
- Cross Site Scripting
- Password Attack
- Ransomware Attack
- Eavesdropping Attack
- AI-powered Attack
- Malware
- Zero-day exploit
- Advanced Persistent Threats
We have Summarized the all top 13 Cybersecurity Attacks below.
1. Phishing Attacks
Phishing is the technique to steal a user’s data from the internet or computer-connected device. Login credentials, credit card numbers, and passwords are usually what such hackers obtain from their victims.
Such criminals use disguise, pretending to be someone their victims can trust. Then they trick them into opening a message, email, or link. Usually, the victim’s system freezes shortly after clicking the link or message, and their sensitive information becomes accessible to the hacker.
For example, you probably receive spam in your email every day. Also, it is very likely that a few of them would have links to buy a product, or read an article. Such spams can be a window for hackers to steal funds, make unauthorized purchases, or take over your entire computer.
Phishing is one security breach that can have disastrous, and long-lasting effects on a victim. There are several types of phishing attacks which include:
Whale Phishing
- Here, high-profiled employees like CEOs are targeted and tricked into making transfers to the attacker
Spear Attack
- This is an email targeted threat to an individual or organization
Pharming
- Pharming is a fraudulent act that directs users to a fake page that looks like the original, to steal from them
- For example, an attacker can create a web page that looks exactly like that of the victim’s bank to trick them into entering their pin
How to prevent phishing scams?
- Know what a phishing scam looks like
- Don’t click on a random link
- Get free anti-phishing add-ons
- Don’t give your information to an unsecured site
- Change passwords regularly
- Don’t ignore updates
- Install firewalls
- Don’t be tempted by pop-ups
- Don’t give out important information unless it is important
- Have a Data Security Platform to spot signs of an attack
2. Man-in-the-middle attack
The man-in-the-middle attack is a security breach where cybercriminals place themselves between the communication system of a client and the server. For example, you are on a call with your boss, and he has just given you some sensitive information over the phone. Hence, in man-in-the-middle attacks, a criminal will be listening to that conversation and obtain the information you spoke about.
Man-in-the-middle is by far the sneakiest attack by criminals. Vulnerable WiFi connections and communication lines are the easiest means to carry out this security breach. The three common types of man-in-the-middle attack are:
Session Hijacking
- In this cyber-attack, the hacker takes control of the session between the network server and the victim
- For instance, the hacker can replace the user’s connection, or even create a fake server and trick the victim into connecting to it
IP spoofing
- This security breach provides access to the hacker by tricking the user into communicating with a known entity
- For instance, a packet of internet addresses, including that of a trusted site like google, can be sent to the victim
Replay
- In this Man-in-the-middle threat, the hacker saves old messages and then uses it later to impersonate the user
- For example, if a hacker gets hold of your Instagram page, he or she can use it to impersonate you
How to prevent man-in-the-middle attacks?
- Strong WEP/WAP Encryption on Access Points
- Strong Router Login Credentials
- Virtual Private Network
- Force HTTPS
- Public Key Pair Based Authentication
3. SQL Injection Treat
SQL is an acronym for Structured Query Language, and an SQL attack is one of the oldest cybersecurity breaches. In SQL you make queries. Therefore, in the SQL injection threat, the attacker sends a malicious query to the device (a computer, phone, etc.) or a server. The server is then forced to expose sensitive information.
For instance, a cybercriminal can create a query that disrupts and gets into the database of your webpage through SQL injection. All the data, like your customers’ details, amount paid, and other confidential information, can then be released by the query.
The daunting part of this cyber-attack is that the attacker can not only get hold of sensitive information but also alter or wipe them completely.
Types of SQL Injection attack
- Intradermal (ID) injection
- Subcutaneous (SC) injection
- Intramuscular (IM) injection
Example of SQL Injection attack
- GhostShell attack: GhostShell targeted 53 universities using the SQL injection and stole 36,000 personal records belonging to students, faculty, and staff.
- Turkish government: RedHack collective used SQL injection to erase debt to government agencies.
- 7-Eleven breach: A team of attackers used SQL injection to penetrate corporate systems, primarily the 7-Eleven retail chain, stealing 130 million credit card numbers.
How to prevent SQL injection attack?
- Validate User Inputs
- Sanitize Data By Limiting Special Characters
- Enforce Prepared Statements And Parameterization
- Use Stored Procedures In The Database
- Actively Manage Patches And Updates
- Raise Virtual Or Physical Firewalls
- Harden Your OS And Applications
- Reduce Your Attack Surface
- Establish Appropriate Privileges And Strict Access
- Limit Read-Access
4. Distributed Denial of Service (DDoS) Attack
This cyber-attack overwhelms a network, system, or computer with unwanted traffic. The attacker bombards the system or server with high-volume traffic, that its bandwidth and resources cannot handle. Hence, they will not be able to respond to requests. For example, a gardening website that notices a sky-rocketed number of visits of unknown users in a day may be under a DDoS attack.
Distributed Denial of Service attacks does not usually result in identity theft or loss of vital information. However, it will cost a lot of money to get the server running again.
5. Drive-by Attack
Drive-by attacks are security threats that download unwanted materials from a website. It is also one of the most common ways of spreading malware. All the hacker has to do is to plant code on the page. You have probably seen a few pop-ups that do not relate in any way to what you are searching on the internet. Such pop-ups are drive-by attacks.
Unlike other cyber-attacks, a drive-by download does not need you to do anything to enable the attack on your computing device. The best way to protect yourself from such threats is to update your internet browsers frequently. Also, do not leave too many apps and programs on your devices open.
6. Cross-Site Scripting (XSS)
Cross-site scripting is a cyber-attack where an attacker sends malicious code to your company’s website. It is an attack that can happen only when a website allows a code to attach to its own code. The attacker bundles together two scripts and send to the victim. As soon as the script executes, the attacker receives a cookie. With this type of cyber-attack, hackers can collect sensitive data and monitor the activities of the victim.
For example, if you see a funny-looking code on your government’s page, then an attacker is probably trying to get access to your device through Cross-Site Scripting.
How to prevent cross-site scripting attack?
- Filter input on arrival.
- Encode data on output.
- Use appropriate response headers.
- Content Security Policy.
Also Read: Preventing Cloud Security Threats
7. Password Attack
As its name implies, password attack is an attempt to steal passwords from a user. Since passwords are the most common authentication means, attackers are always on the lookout for ways to use this cyber-attack. Two common techniques they use to get a user’s password are:
Brute-force guessing
- This entails using different random words, hoping that one of them would be the correct password
- If the hacker knows his or her victim, they can apply logic while guessing and try the person’s title, name, job, or hobbies as the password
Dictionary Attack
- In this case, the hacker uses some of the common passwords to gain access to the user’s device
- For instance, 1234 or ‘abcde’ are passwords that a lot of people use on their devices and these two are at the top of the list of common ones an attacker will try out
To protect yourself from either of these two types of password attacks, implement a lockout policy to your cybersecurity.
8. Ransomware Attack
One cyber threat with scary consequences is the ransomware attack. Moreover, in this type of security breach, the malware prevents users from accessing the data they stored on a server or database. The hacker then sends out a threat demanding a ransom, else they would expose or delete the data.
9. Eavesdropping Attack
Other names for eavesdropping attack are snooping, network security threat, or sniffing. It is very similar to the man-in-the-middle attack, but it does not allow a secure connection between the user and a server. Theft of data and information occurs after you send them out, so they do not get across to the server.
Unsecured and weak network transmissions allow this security breach to thrive. Any device within the network is susceptible to an eavesdropping attack from hackers.
10. AI-Powered attacks
Artificial intelligence (AI) has been making ground-breaking success in recent years. Almost every gadget has some application of AI in it, which heightens the scare of an AI-powered cyber-attack. Such security threats will have the most devastating effects as autonomous cars, drones, and computer systems can be hacked by artificial intelligence. AI can also shut down power supplies, national security systems, and hospitals.
11. Malware
Malware is a common type of cyber threat, defined as malicious software which gets installed into the system when the user clicks on a dangerous link or email.
What is Malicious Software (Malware)? Malicious software commonly known as malware is any software that brings harm to a computers system. Malware can be in the form of worms, viruses, trojans, spyware, adware and rootkits, ransonware, etc., which steal protected data, dlete documents or add software not approved by a user.
A most common type of malware threats are:
- Viruses: The virus replicates itself, infect application in the computer system. Viruses can also attach themselves to executable code with a .exe extension, thus creating a decoy that carries the virus. Eg: Melissa, virus, 1999: The Melissa virus was spread by email, using malicious attachment and infected thousands of computers worldwide by the end of 1999. Reports from that time say that it infected many companies, causing losses estimated at USD 80 million.
- Trojans: Trojan is commonly used to establish a backdoor to exploit the attackers. Ex: Zeus, trojan, 2007 Zeus is a trojan distributed through malicious files hidden in emails and fake websites, thus attacking major companies such as Amazon, Bank of America and Cisco. The damage caused by Zeus and is estimated at more than USD 100 million.
- Worms: Worms are often installed through email attachments. Ex: Stuxnet, worm, 2010 The Stuxnet was being used in a political attack, in 2010. This super-sophisticated worm has the ability to infect devices via USB drives, so there is no need for an internet connection.
- Ransomware: This is a type of malware that uses crypto-viral extortion to denies access to the victim data. Ex: Covid Lock, ransomware, 2020 This covid Lock ransomware has infected many victims via malicious files promising to offer genuine information about COVID-19 disease.
How to prevent malware?
- Regularly update your computer and software.
- Use a non-administrator account whenever possible.
- Be careful while opening unknown email attachments or images.
- Don’t trust pop-up windows that ask you to download software.
- Limit your file-sharing.
12. Zero-day exploit
A zero-day attack is an attack done by hackers when the network, hardware or software vulnerability is announced publicly. They make use of this time to exploit the vulnerabilities before the solution is implemented.
Why is it called a Zero-day attack?
After announcing the vulnerabilities publicly, security professionals have “zero-day” to fix the problem, and this is when attackers try to steal information. This is the reason for calling this attack a “zero-day” attack.
Examples: In 2017, Microsoft Word was hit with a zero-day exploit that compromised personal bank accounts. Here victims were common people who opened malicious word document that displayed a” load remote content” prompt and requested external access from another program. This is when Microsoft word was hit by a “zero-day” attack.
How to prevent a Zero-Day Attack?
- Use an advanced, proactive email security solution
- Educate users
- Deploy a web application firewall
- Implement network access control
- Use IPsec
13. Advanced Persistent Threats (APT)
An advanced persistent threat occurs when an attacker gains unauthorized access to a system or network and remains undetected for a long duration.
The goals of APTs are:
- Cyber Espionage
- eCrime for financial gain
- Hacktivism
- Destruction
Examples: This attack is usually sponsored by nations or very large organizations.
One such example is Stuxnet, In 2010 U.S. and Israeli cybersecurity forcers attacked the Iranian nuclear program to slow down the country’s ability to enrich uranium and took down Iran’s nuclear program, and Hydraq. Stuxnet was not any virus or a worm, instead, it was computer hijacks that stole information and physically destroyed the centrifuges that enriched the uranium.
How to prevent Advanced Persistent Threats (APT)?
- Install a Firewall
- Enable a Web Application Firewall
- Install an Antivirus
- Implement Intrusion Prevention Systems
- Create a Sandboxing Environment
- Install a VPN
- Enable Email Protection
Sources of cyber threats
It is important to identify the source of cyber threats to understand where is this threat coming from, who has done this and why. Some of the common sources of cyber threats include:
- State-sponsored
- Terrorists
- Industrial spies
- Organized crime groups
- Hackers
- Hacktivists
- Malicious insider
- Cyber espionage
Impact of Cyber Attacks
A lack of focus on cybersecurity can most often cause serious damages in various ways including:
- Economic costs: This involves theft of intellectual property, corporate information, disruption in trading and the cost of repairing damaged systems.
- Reputational costs: This includes loss of consumer trust and loss of future customers to competitors due to poor media coverages.
- Regulatory costs: GDPR and other data breach laws can impact an organization to suffer from regulatory fines or sanctions due to these cybercrimes.
Given the nature of these cyber-attacks, it is vital for all businesses, regardless of the size, to understand cybersecurity threats and methods to mitigate them. This includes regular training on the subject, and a framework to work with – that aims to reduce its risks of data leaks and breaches.
Importance of Cybersecurity
In the present day world, everyone benefits from advanced cyber defense programs. Apart from businesses and organizations, at an individual level, a cybersecurity attack can result in everything from identity theft, extortion attempts, to the loss of basic important data like family photos. Cybersecurity is extremely essential because it encompasses everything that includes protecting our sensitive data, Personally Identifiable Information (PII), Protected Health Information (PHI), personal information, intellectual property data, and many more from theft and damages attempted digitally by criminals.
Cybersecurity risk is increasing, driven by global connectivity and usage of cloud services to store sensitive data and personal information. Poor configuration of cloud services paired with increasingly sophisticated cyber-criminals means the risk that your organization suffers from a successful cyber-attack or data breach is on the rise. A successful cybersecurity approach contains numerous layers of protection that is spread across the computers, networks, and programs. In an organization, hence, it is essential to ensure that the people, the processes, and technology in it must all complement one another in order to create an effective defense from cyber attacks.
To sum up, listed above are some of the cyber-attacks that you can face as a business owner or user of technological devices. The data, accounts, passwords, and sensitive information that can be lost, deleted, or made public by cyber-attacks is alarming. Tech companies to do not get to exempt from the scare. Facebook had a security breach where hundreds of millions of Facebook user records were exposed on the Amazon cloud server, and Equifax spent an estimated $439 million to recover from a cyber breach.
Cyber threats are attacks that you should stand up to and protect yourself and the company from the harm that comes with it.